Real Estate Cybersecurity for Property Managers: What’s at Stake?
Think for a moment about the data that’s collected on the standard rental application or lease agreement. If one of these forms were to make it into the wrong hands, an identity thief would instantly have access to tenants’ full names, social security numbers, current and former addresses, dates of birth, places of employment, credit history, contact information, and more. It’s all of the information that they would need to piece together the identities of countless people who trusted you with their information.
Chart of Accounts
Want clearer, cleaner books? What about a more useful view into your properties or just easier accounting in general?
Get the GuideNext, think about the financial transactions that pass through your office each month. From rent payments and security deposits to payments to contractors, think about the impact that it would have on your business for the security of those accounts to be compromised. How long would it take for you to get back on your feet?
What about the years’ worth of taxes and property records that you keep on file? What kind of havoc could a cybercriminal wreak on your business if they had access to this information?
A Multifamily Executive article observed:
“Maybe if we don’t talk about the potential for data breaches in the apartment industry, the identity thieves won’t know we’re here. That seems to be the attitude among apartment operators when it comes to data security and the potential for resident information being compromised or stolen.”
Why does cybersecurity fail to garner the concern it warrants among property managers and landlords? First, there’s the misconception that small businesses can fly under the radar. Second, there’s a fundamental misunderstanding of the value of the data that we possess. Let’s dig into both of these important topics to set the facts straight.
Cybersecurity 101: Find out what property managers need to know on the #BuildiumBlog! Share on X
Misconception #1: “My Business is Too Small to be Targeted by Hackers”
First, let’s go over some sobering statistics:
- 71% of cyberattacks take place in companies with less than 100 employees.
- 55% of small to medium-sized businesses were attacked between mid-2015 and mid-2016. Each of these companies lost over 5000 individual records, spent an average of $880k as a result, and incurred $955k in damage.
- 6 in 10 small companies go out of business within 6 months of a cyber attack.
Why is this the case? Small businesses are significantly less likely than larger companies to have a security expert on staff—in fact, if you have IT personnel at all, you’re in the minority. 67% of small businesses state that insufficient personnel are their top barrier to improving their cybersecurity, while 54% report that their budget is the problem. 58% of small businesses are concerned about cyber attacks, but 51% admit that they don’t spend a single dollar on risk mitigation.
So property managers and landlords are already attractive to cybercriminals because of the large sums of money they process and the sensitive data they collect—and when that’s combined with a dearth of security measures, it creates a perfect storm. The odds are that you’ve already been attacked—and if you’ve managed to evade it so far, your luck can’t last forever. It’s time to invest in prevention efforts, even if your budget’s tight.
Keep in mind that cyberattacks aren’t the sole concern here. Just 48% of data breaches in small businesses are perpetrated by malicious hackers—meaning that just over half of all data breaches are a result of negligence on the part of employees and vendors. Employee training and tough conversations with the vendors you work with will be key in preventing security incidents in your company. We’ll go over what you need to do to prevent a nightmare from happening in the second half of this post.
6 in 10 small companies shut down within 6 months of a cyberattack. Find out more on the #BuildiumBlog! Share on X
Misconception #2: “Hackers Won’t Be Interested in the Data My Business Possesses”
The primary reason that small businesses don’t allocate more of their budget to cybersecurity measures is that they don’t understand how attractive their data is to cybercriminals. However, a recent study found that 68% of small businesses store email addresses, 64% store phone numbers, and 54% store billing addresses—all of which is digital currency that’s in high demand. This type of data—known as personally identifiable information (PII)—is sold between hackers on the “dark web,” the digital black market for stolen identities, fake passports, hitmen, and so, so much more.
Every time there’s a data breach, there are thousands—perhaps millions—of people willing to pay for this leaked information. Once hackers get their hands on your log-in information, they’ll proceed to test it on thousands of websites. They’re not doing this manually, either—they have software that does it for them instantaneously. So by using the same log-in information across countless sites, when one company inevitably has a breach, you’ve given hackers the keys to all of your accounts in one fell swoop. You can find out if your account info has been leaked on the site Have I Been Pwned?
There are also people working to piece together information that they collect about you from multiple online sources into whole identities—from your photo and address to your social security number and date of birth. In the social media era, this information is surprisingly easy to gather—and as you can imagine, it’s extremely attractive to identity thieves. If a breach occurs in your company, everyone whose information is stored in your databases is exposed to a great deal of risk—and you’re exposed to a tremendous amount of liability.
Don't fall victim to cybersecurity misconceptions--find out what they are on the #BuildiumBlog! Share on X
Common Real Estate Cybersecurity Attacks
Here are the most common attacks that your business should familiarize itself with and protect itself against:
#1: Email Scams
You’ll receive an email inviting you to participate in a scam masquerading as a fantastic deal. You can recognize this type of attack because it’ll require you to provide money or bank account info up-front—and the fact that the offer is coming from a complete stranger with questionable grammar.
Here’s an email scam example that I pulled from my own inbox:
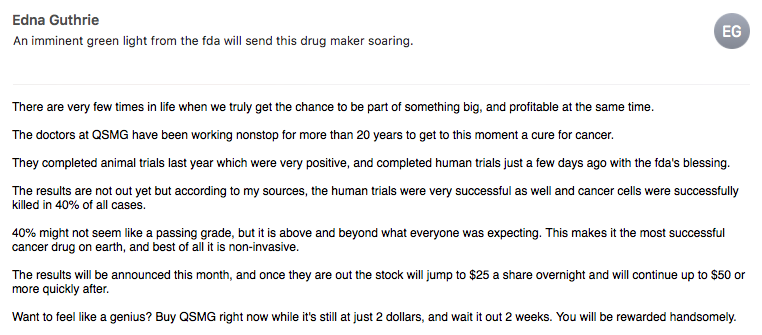
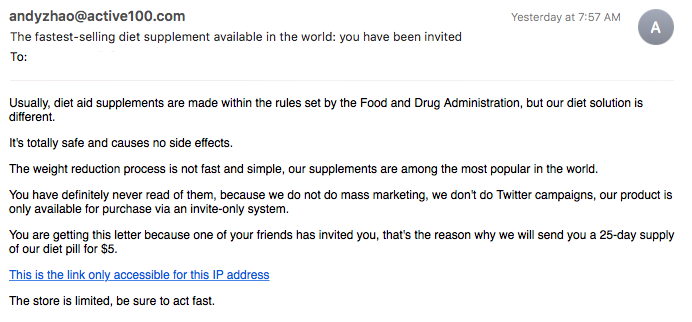
Here’s another email scam example:
#2: Phishing
You’ll receive a transactional email letting you know that there’s an issue with one of your accounts that requires you to sign in. However, the email is not actually from the company it claims to be from; so when you enter your account details, you’re giving sensitive data directly to a cybercriminal. Keep reading for tips on how to recognize and avert phishing scams in the next section.
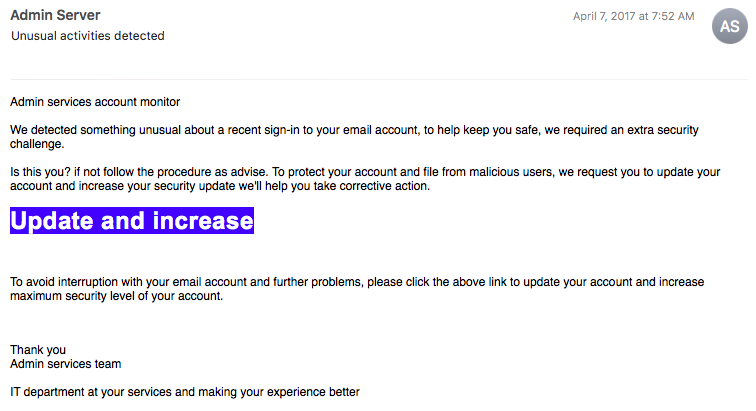
Here’s a phishing example from my inbox:
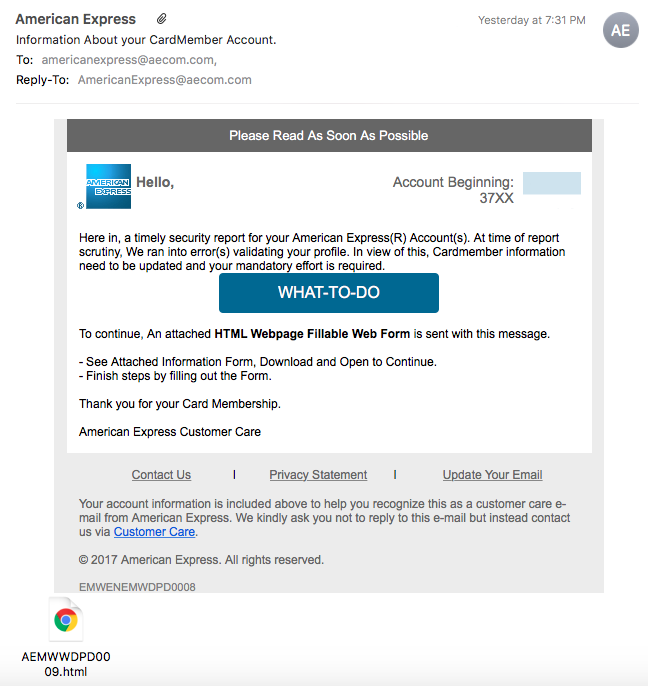
Here’s a sneakier phishing attack masquerading as a transactional email from American Express. This could trip you up if you have an AmEx account; but if you take a moment to carefully read the message, you’ll realize that something seems fishy.
#3: Viruses
Viruses come in a variety of forms, but they always involve you downloading a file that performs a function on your computer that you didn’t intend. A common one right now will pop up in your browser letting you know that you need to update your Flash player. However, rather than taking you to Adobe’s website to download the latest version, it’ll trick you into downloading a file from a different site (such as flash.com). Once it’s on your computer, it could cause scores of unwanted ads to pop up, steal your personal information, or more potentially dangerous actions.
#4: Trojan Horses
Trojan horses, like their namesake, hide within computer programs that you’ve installed so you don’t notice that they’ve snuck in. After being embedded into legitimate programs by hackers, these files install themselves onto your computer. They can then steal information, delete files, hijack your webcam, and more.
#5: Botnets
Botnets are “software robots” controlled by hackers that can be used to spread malware throughout your network via emails from your device. They can also be leveraged (along with other people’s devices) as part of a distributed denial-of-service (DDoS) attack—the massive cyberattacks that occasionally take down business or government websites.
Learn to recognize the 5 most common cyberattacks on the #BuildiumBlog now! Share on X
Now that you understand the dire importance of real estate cybersecurity for property managers, which measures can you take to improve? Check out Data Breach Prevention for Property Managers for step-by-step instructions on locking down your company’s data, networks, emails, mobile devices, and more.
Read more on Mixed Portfolio